Jump to
Stay tuned for
more insights
Follow us on
Username Enumeration
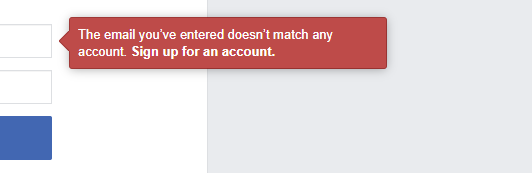
What is username enumeration?
Username enumeration is a common application vulnerability which occurs when an attacker can determine if usernames are valid or not. Most commonly, this issue occurs on login forms, where an error similar to “the username is invalid” is returned.
An attacker can exploit this behavior by using lengthy lists of common usernames, known names, and dictionary words to observe the application response to all. With those results, the attacker can then infer which usernames are valid.
Dangers of Username Enumeration
Although username enumeration is not itself always a high risk issue, it does provide an attacker valuable information for other attacks.
1. Brute forcing Passwords
Once an attacker has a list of valid usernames, they can then easily target those users for common passwords. On a large platform, how many users have a password of Password@123?
2. Credential Stuffing
An attacker can use the usernames identified to search existing compromised databases for passwords. Chances are your users have identical usernames on other platforms, and may have used identical passwords as well.
3. Social Engineering
After learning usernames, an attacker can likely identify the names of those users and attempt to contact them directly with social engineering campaigns.
Username Enumeration Mitigation
“Don’t inform users the account is invalid” is the common recommendation, however there are some very important guidelines to follow.
Identical Server Responses
The industry standard, fool-proof recommendation to mitigate username enumeration is to return identical responses for “valid user/wrong password” and “invalid user” login requests.
It’s important to mention these responses must be identical in their entirety. The HTML content must be exactly the same. In a recent penetration test of ours, the following responses were found to create a username enumeration vulnerability:
Valid User/ Invalid Password
- The username or password is not valid.
Invalid User
The username or password is not valid.
As shown above, one response includes a line break (not visible in the user’s browser). Although the two responses are visually the same, practical exploitation of username enumeration does not involve any visual methods. The response data is simply gathered from a large number of responses, and then data separated from known invalid responses.
Rate Limiting
We recommend using rate limiting only when all other measures are truly deemed infeasible due to business requirements or technical limitations.
Be aware that rate limits can be bypassed by using a large network of IPs which are widely and easily available to most seasoned attackers. They can also be bypassed with “low and slow” attacks, where requests are sent over a long period of time.
Conclusion
Application owners must balance usability and security requirements. Our opinion for the vast majority of applications is this is an issue which should be remediated. In some circumstances, non-sensitive applications may choose to accept this risk of this issue. For assistance with your application, check out our pentest services and drop us a line.
