Jump to
Stay tuned for
more insights
Follow us on
HTTP Request Smuggling (AWS)
Applications undergoing an AWS pentest are frequently flagged as vulnerable to HTTP Request Smuggling.
This is often because an Elastic Load Balancer is not configured with the Drop Invalid Header Fields Disabled option.
What is HTTP Request Smuggling?
Request smuggling exists because HTTP headers are parsed differently by application layers.
By creating a malformed request with multiple content length fields, an attacker can cause two layers to treat a request differently.
Ultimately, this can allow an attacker to bypass authentication and hijack other user’s sessions.
Drop Invalid Header Fields Disabled
AWS ELB’s do not drop requests with invalid header fields by default. However, the vast majority of applications behind a load balancer will want to enable this behavior.
Invalid headers are required to create a desync attack and exploit HTTP request smuggling.
Using an ELB to drop invalid headers is a nice way to normalize HTTP headers and prevent ambiguous handling by all layers down the chain.
Vulnerability Remediation
This vulnerability can be remediated easily from the AWS console. It is always ideal to also implement this configuration in deployment scripts used.
From Within the AWS Console
Navigate to https://console.aws.amazon.com/ec2/ and select Load Balancers from the left navigation window.
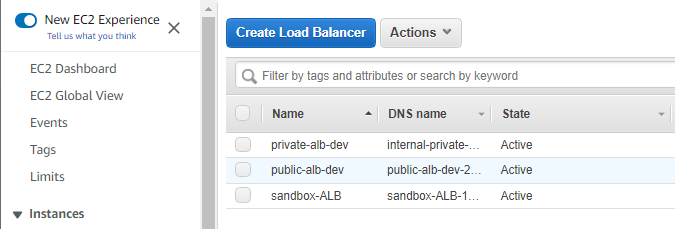
Right click on the Load Balancer and select Edit Attributes.
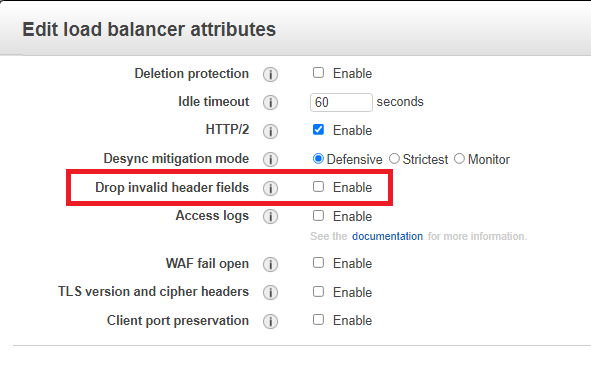
Toggle Drop Invalid Header Fields Disabled to Enabled and save.
