1 – You.
You are the first and most important step in an Android vulnerability assessment. Mobile vulnerability assessments require a keen eye to evaluate application functionality and design. This means identifying controls which are performed on the client itself. Once you have performed a full review of an application and determined exactly what controls you want to subvert, then you can begin to use tools to manipulate them. Dynamic scanners used in web applications will likely not exist in the near for mobile applications. Serious vulnerabilities in mobile applications often stem from poor design and are thus highly subjective. Tools will likely never be able to identify these themselves. For now, we must use our brains.
2 – Virtuous Ten
http://www.virtuous-ten-studio.com/ When reverse engineering and subverting client side controls, Virtuous Ten is the way to go. Client side controls on the Android platform can generally be defeated most easily by modifying and repackaging smali code. Virtuous Ten provides an easy to use interface to import the applications APK, disassemble the application, view the contents of the package, and rebuild the application after modifying code. Virtuous Ten also allows for Java to be generated for smali documents, allowing an easier way to read many code pages. Packages can also be seamlessly pushed to your testing device or emulator through ADB. Virtuous Ten is free for personal use and has an affordable license for commercial use. 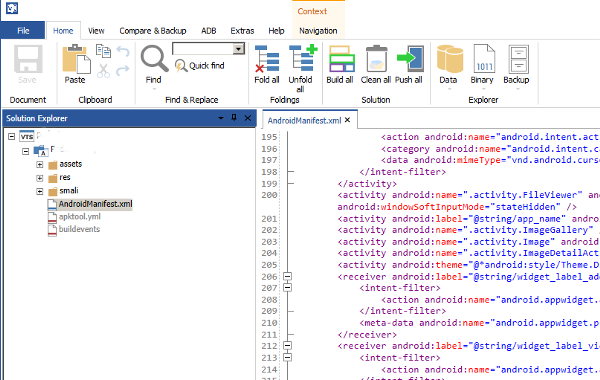
3 – MWR Labs Mercury
http://labs.mwrinfosecurity.com/tools/2012/03/16/mercury/ Mercury provides an easy and powerful way to interact with application IPC endpoints. Assessing the integrity of an application from attacks launched from malicious apps is a major part of any Android application vulnerability assessment. Ethical hacking service providers must ensure that other apps on the device cannot steal application data or invoke the application in insecure ways. Mercury allows for a tester to use an agent to simulate any attacks they wish, and operate as an unprivileged but malicious app. 
4 – BURP
http://portswigger.net/burp/download.html The vast majority of mobile applications communicate with HTTP. Although mobile apps have the capability to use almost any network based protocol, most of the time you will find yourself testing applications using HTTP. For this we can use what many of us are accustomed to, a simple network proxy. Burp has simple but powerful features to intercept, modify, and replay traffic sent by the client. This can be used to bypass client side controls as well as attack server side application components. 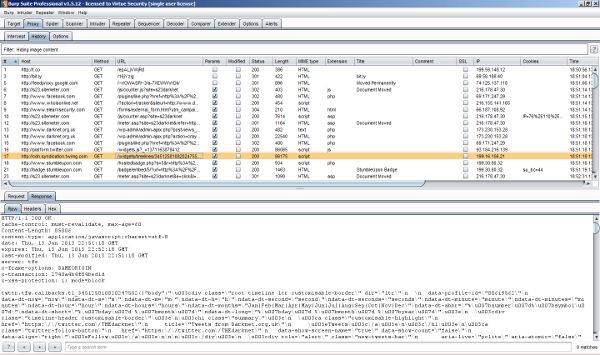
5 – Mallory
https://github.com/intrepidusgroup/mallory Intrepidus’s Mallory is a powerful TCP and UDP proxy. Applications implementing their own protocols via raw sockets will require a much more flexible proxy. Mallory includes plugins to handle many existing non-HTTP protocols, however also provides the capability to write your own plugins for unsupported or custom protocols. Mallory must function as a standalone gateway, but can be configured in several fashions. We find it easiest to run Mallory on a separate device, and either act as a wifi hotspot or as a VPN gateway, and tunnel the Android device through PPTP.