Many vulnerability scanners will raise false positives regarding outdated installations of OpenSSH on Ubuntu; notably issues similar to: * OpenSSH < 7.0 Multiple Vulnerabilities * OpenSSH < 6.6 Multiple Vulnerabilities A thorough penetration test should weed out false positives of these issues, however they are a common occurrence in assessments relying on automated tools. In this example we will look at a fully patched Ubuntu 14.04 server with OpenSSH installed and show how to properly validate this issue. To start let’s grab the banner of the host in question:
$ nc 10.0.1.35 22
SSH-2.0-OpenSSH_6.6.1p1 Ubuntu-2ubuntu2.3
This banner reveals a number of configuration details about the server, but we’re only concerned right now with the very last flag on this example. The ‘2.3’ on the right is the internal Ubuntu patch level, which we can use to verify what vulnerabilities have been patched. First we should find out what the latest patch level is; to do this we can reference the following URL:
http://packages.ubuntu.com/search?keywords=openssh-server
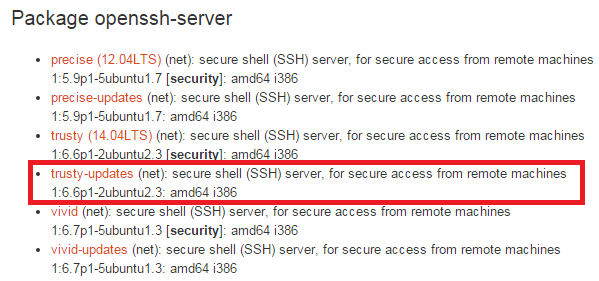
This will lead us to the following URL where we can look at the changelog: http://packages.ubuntu.com/trusty-updates/openssh-server
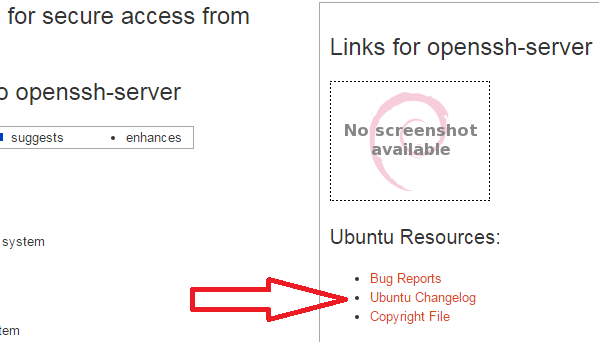
Which then brings us to the changelog for the latest Ubuntu openssh-server patch: http://changelogs.ubuntu.com/changelogs/pool/main/o/openssh/openssh_6.6p1-2ubuntu2.3/changelog
openssh (1:6.6p1-2ubuntu2.3) trusty-security; urgency=medium
* SECURITY REGRESSION: random auth failures because of uninitialized
struct field (LP: #1485719)
- debian/patches/CVE-2015-5600-2.patch:
-- Marc Deslauriers <marc.deslauriers@ubuntu.com> Mon, 17 Aug 2015 21:52:52 -0400
openssh (1:6.6p1-2ubuntu2.2) trusty-security; urgency=medium
[..]
* SECURITY UPDATE: X connections access restriction bypass
- debian/patches/CVE-2015-5352.patch: refuse ForwardX11Trusted=no
connections attempted after ForwardX11Timeout expires in channels.c,
channels.h, clientloop.c.
- CVE-2015-5352
Here we have verification that the 2.3 patch includes an improved fix for vulnerability CVE-2015-5600 and that the 2.2 patch included updates for CVE-2015-5352 as well. This is a critical comparison that should be made to vulnerabilities raised by automated scanners. If no verification can be obtained from this method, the comparison should default to the OpenSSH version (6.6 in this case) and CVE details. If the OpenSSH server is found to be out of date it can be easily upgraded with Ubuntu’s package management system.
$ sudo apt-get update
$ sudo apt-get upgrade