Jump to
Stay tuned for
more insights
Follow us on
Locating Rogue WiFi Access Points
During a wireless ethical hacking assessment, one objective should always be to identify rogue wireless access points. This ensures that an attacker outside the building cannot use a wireless “backdoor” to access the internal network. Whether a malicious employee has planted an access point (AP), or a well-meaning employee has insecurely configured an AP for their group, a rogue AP can present a very serious risk for the organization. There are two common ways of identifying these devices. The first is by performing network scans of the internal network, and comparing all MAC addresses to known vendors of wireless equipment. This method is not reliable since MAC addresses can be easily changed from within the AP configuration itself. Because of this we will not cover the network scanning method. The second method, which we will cover, is to use radio frequencies to physically locate rogue WiFi devices. By attempting to follow signal strength with a granular signal reading, we can lead ourselves within several meters of the transmitter. With a bit of persistence, we can physically locate the device over 95% of the time. Resources airodump-ng can be downloaded with the aircrack-ng suite, or can be found pre-installed with backtrack. Summary To determine where rogue access points exist we must essentially “triangulate” the signal of devices which do not have a known ESSID or BSSID. To see this, along with the corresponding signal strength, tools such as airodump-ng can be used to monitor the WiFi spectrum. Once we have the tool running, can take a sample readings and continuously change our position based on whether we are getting “hot” or “cold”.
If we divide a given area into sections and take sample readings in each section, we can quickly clear an area if no suspicious devices are seen. To begin, we will run the following command: # airodump-ng mon0
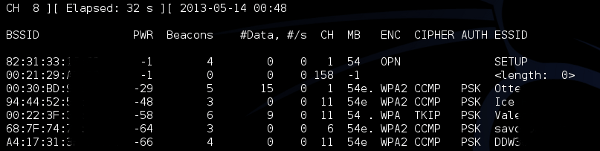
If a suspicious device is seen with a relatively strong signal (-60db or less), we can lock on to the device’s channel and filter by the suspicious BSSID. This will give us a much more granular reading of the device’s signal strength since airodump will no longer be channel hopping across other channels. To do this we must take note of the channel displayed and run the following command: # airodump-ng -c 6 –bssid 00:23:69:NN:NN:NN mon0
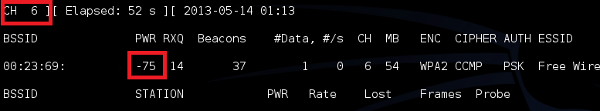
Take note that we are now locked on channel 6 and only viewing the device in question. We will now be able to see if walking in a particular direction is bringing us closer or further from a device. Antenna Type While it’s commonly suggested to use directional antennas for this exercise, we find omni-directional antennas best suited for complex office structures and densely populated areas. Directional antennas require the antenna to be pointed directly at the AP, however, signals can be greatly disturbed by reflecting walls, doors, and other objects. Additionally, we recommend using low to medium strength antennas. Using high powered antennas will introduce excessive noise from distant APs. Obstructions Keep in mind that the type of internal construction on building walls can cause drastically different levels of interference. Elevators, microwaves, double paned glass, and adjacent bodies of water can all affect radio signals. Non-Broadcasting ESSIDs Not all APs will be configured to broadcast ESSIDs. Keep in mind that although the ESSID is not broadcasted, beacons are still sent by the AP. Most APs will broadcast at a rate of 1 beacon per 100ms, the ESSID will not be sent in the beacon, but can still be easily obtained when a client joins the network. External Signals Densely populated areas such as New York City, Chicago, and Hong Kong will often have significant external wireless traffic. Determining which signals are outside the facilities is critical. One way to do this is to estimate the size of the broadcasting radius. Consider the image below:
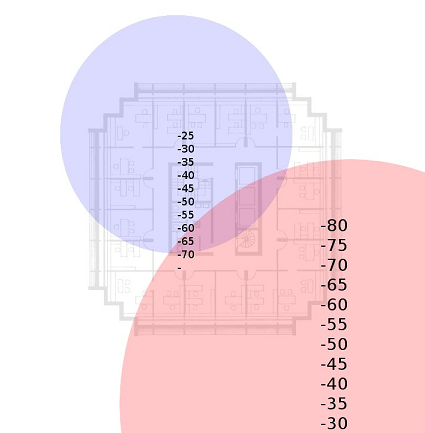
By measuring the distance of range of a signal you can approximate the location of the device. A very powerful external device will often yield a “warm” signal for a large area, but will not have a very strong signal in your facilities.
