Jump to
Stay tuned for
more insights
Follow us on
Enable Network Level Access For Windows RDP
Chances are you may have arrived here after a vulnerability scan returns a finding called “Terminal Services Doesn’t Use Network Level Authentication (NLA)”. The default configuration of Windows 7, 2008, and 2012 allows remote users to connect over the network and initiate a full RDP session without providing any credentials. This allows an untrusted user to land on the system login page as shown below:
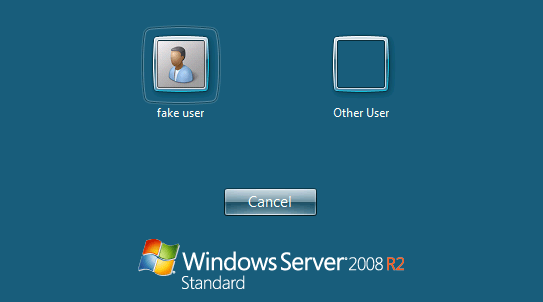
Several risks are associated with this functionality; an attacker is now able to: * Accurately fingerprint the version of Windows * Potentially identify user accounts on the system * Leverage the RDP service to consume excessive system resources The default configuration of RDP is similar to letting anyone into the lobby of your building; while they may not have keys to apartments, we generally don’t want strangers milling around the lobby to gather information if it can be avoided.
Remediation
To enable network level access on Windows 2008 R2 we can do the following:
1. Open the Group Policy Editor by typing ‘gpedit’
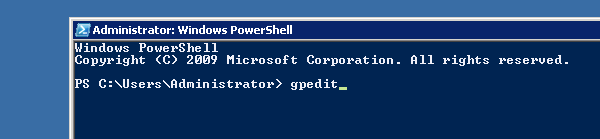
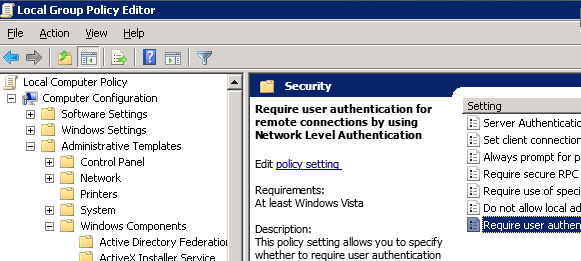
2. Navigate to the following:
- Computer Configuration
- – Administrative Templates
- — Windows Components
- — Remote Desktop Services
- —- Remote Desktop Session Host
- —– Security
7. Doubleclick on “Require user authentication for remote connections by using Network Level Authentication”
8. Check ‘Enabled’. Apply. Save.
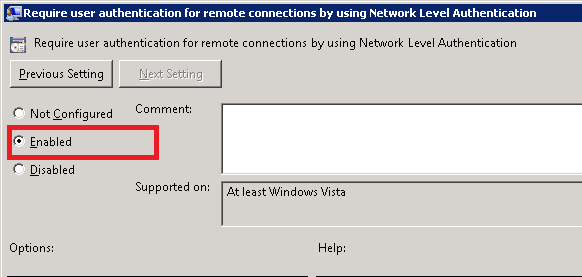
Changes are immediate, no reboot is required. Network Level Access should now be enabled.
Verification
One of the quickest and easiest ways to verify if NLA is to use the ‘rdesktop’ tool packaged with
Kali Linux. When NLA is properly enabled, you will get the following error:
root@kali:~# rdesktop 10.0.1.73
Autoselected keyboard map en-us
ERROR: CredSSP: Initialize failed, do you have correct kerberos tgt initialized ?
Failed to connect, CredSSP required by server.For long term solutions to this issue, organizations may wish to make this change part of a hardened standard image used to provision new servers.
